Which of the Following Best Describes Role-based Access Control
Azure RBAC is an authorization system built on Azure Resource Manager that provides fine-grained access management of Azure resources. Role-Based-Access-Control RBAC is a policy neutral access control mechanism defined around roles and privileges.
DAC is based on the owner of the resource allowing other users access to that resource.

. C Access to resources is decided by the system based on the concept of subjects objects and labels. Authentication confirms the identity of the user by validating login credentials such as the user name and password. Consider a process for employee review that includes an assignment to authorize a.
What I mean by role is the functions that an. Which of the following best describes an access control mechanism that allows the data owner to create and administer access control. Which of the following best describes NFS.
MACs Mandatory Access Control RBACs Role Based Access Control LBACs List Based Access Control DACs Discretionary Access Control. RBAC is an access-control model that organizes users into roles and assigns permissions to each role as appropriate. One of the most challenging problems in managing large networks is the complexity of security administration.
D RBAC Role Based Access Control list. The Pega Platform implementation of role-based access control is based on two factors. It uses global rules applied to all users equally.
Employees are only allowed to access the information necessary to effectively perform their. Which of the following best describes a rule-based access control model. Which of the following best describes an access control mechanism that allows the data owner to create and administer access control.
An application layer protocol that is used to retrieve information from network devices. In Pega Platform the operator ID record contains information needed to authenticate a user. Its important to remember that not every employee needs a.
Which of the following best describes role-based access control. Users in other roles that are not granted permission are prohibited from authorizing raises. It is an approach to implement mandatory access control MAC or discretionary access control DAC.
The roles in RBAC refer to the levels of access that employees have to the network. In computer systems security role-based access control RBAC or role-based security is an approach to restricting system access to authorized users. MAC Mandatory Access Control DAC Discretionary Access Control and RBAC Role Based Access Control.
You can satisfy common security requirements by controlling the application features and functions users can access. Which of the following best describes an access control mechanism in which access control decisions are based on the responsibilities that an individual user or process has in an organization. 2 Which of the following best describes an access control mechanism in which access control decisions are based on the responsibilities that an individual user or process has in an organization.
A The information owner decides who has access to resources. RBAC provides fine-grained control offering a simple manageable approach to access management that is less error-prone than individually assigning permissions. Web server Application Database Programmer.
A directory query protocol that is based on X 500 C. Role-based access control C rule-based access control. 21 which thread is NOT considered a social engineering.
The three basic access control mechanisms are. A role-based access control model can group users into roles based on the organizations hierarchy and it is a nondiscretionary access control model. Role-based access control model.
The components of RBAC such as role-permissions user-role and role-role relationships make it simple to do user assignments. RBAC Role Based Access Control 1 Attachment. Role-Based Access Control RBAC As you can probably guess from the name role-based access control gives access permissions based on user roles.
Azure role-based access control Azure RBAC helps you manage who has access to Azure resources what they can do with those resources and what areas they have access to. 5 steps to simple role-based access control RBAC is the idea of assigning system access to users based on their role in an organization. A nondiscretionary access control model uses a central authority to determine which objects that subjects can access.
Which of the following is the best choice for a role within an organization using a RBAC model. Role-based access control RBAC also known as role-based security is an access control method that assigns permissions to end-users based on their role within your organization. It uses local rules applied to users individually.
A file-sharing protocol B. With RBAC you can create a role for HR members who are authorized to access compensation information and grant that role permission to authorize employee raises. This model of access control is the most restrictive and has been adopted by US.
Role-based access control RBAC restricts network access based on a persons role within an organization and has become one of the main methods for advanced access control. This project site explains. Role based access control RBAC also called role based security as formalized in 1992 by David Ferraiolo and Rick Kuhn has become the predominant model for advanced access control because it reduces this cost.
Government and military organizations to exercise control of sensitive information. B Access to resources is determined based on the need to know principle. A MACs Mandatory Access Control b RBACs Role Based Access Control c LBACs List Based Access Control d.
Role-based access control RBAC is a policy-neutral access-control mechanism defined around roles and privileges. Role-based access control RBAC Application and data security are major concerns due to the risk of a data breach leading to customer loss and legal or financial penalties. A Phishing B.
Comments 1 please check for explanation.
Policies Vs Standards Vs Controls Vs Procedures

Product Management Scaled Agile Framework

Hear Here At City Of London Build A Diy Audio Tour With Amazon Connect London City Connection Hearing

What Is A Pharmacy Benefit Manager Pbm Truveris
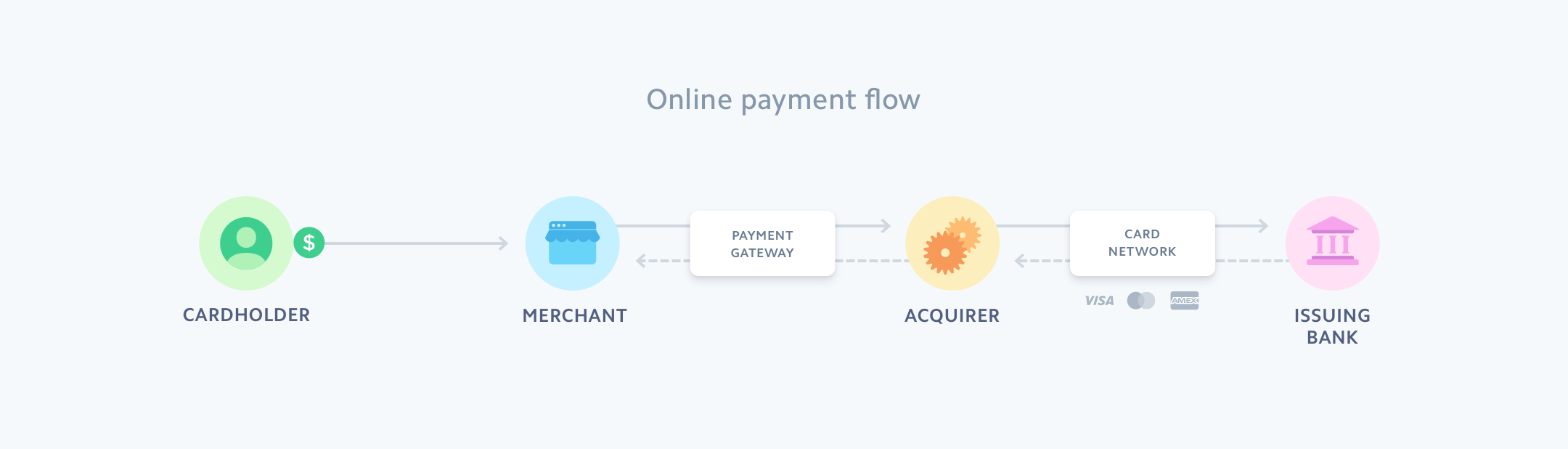
Stripe Introduction To Online Payments

Saas Migration Plan Template Develop A Plan And Schedule To Migrate Users And Data To Any Cloud Based Saas Solution Scope And Process That Describes How User

Equity Vs Equality And Other Racial Justice Definitions The Annie E Casey Foundation
Top 100 Machine Learning Interview Questions Answers Great Learning
/dotdash_Final_Private_Equity_Apr_2020-final-4b5ec0bb99da4396a4add9e7ff30ac03.jpg)
Private Equity Definition How Does It Work

Pin On Software Testing Tutorials
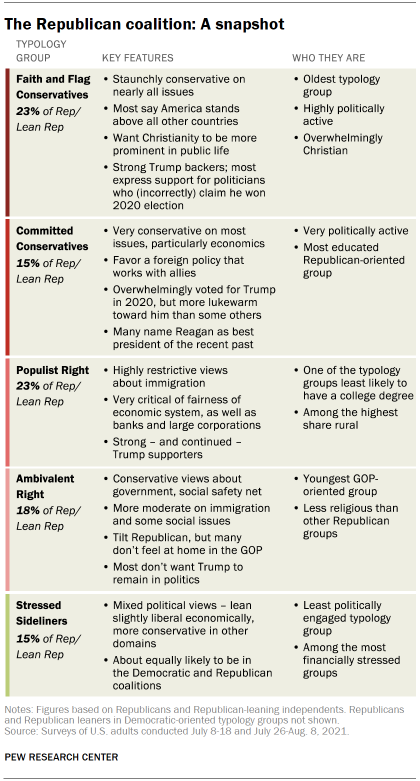
The Republican Coalition Among The U S Electorate Pew Research Center

Policies Vs Standards Vs Controls Vs Procedures
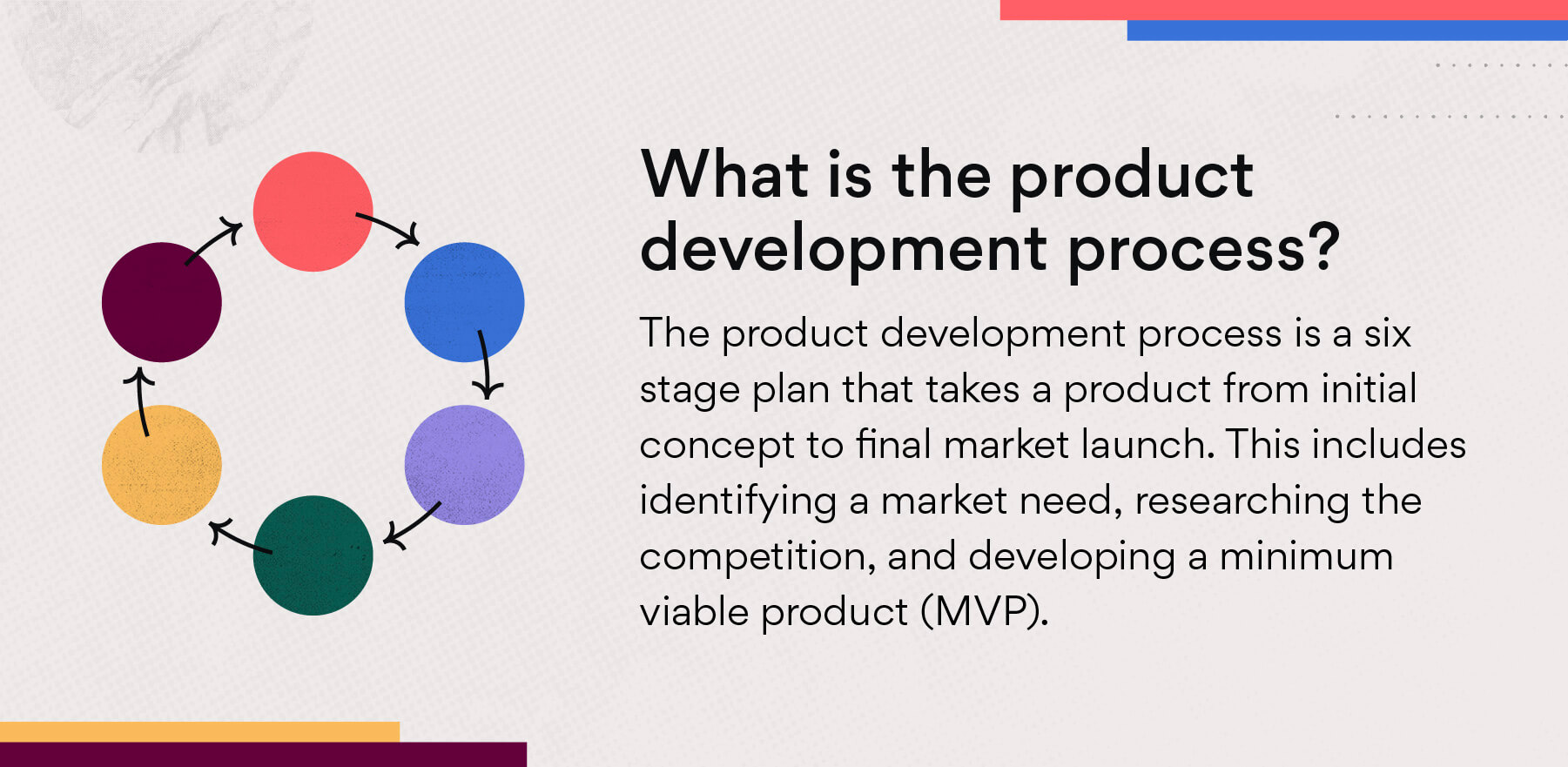
What Is Product Development The 6 Stage Process Asana
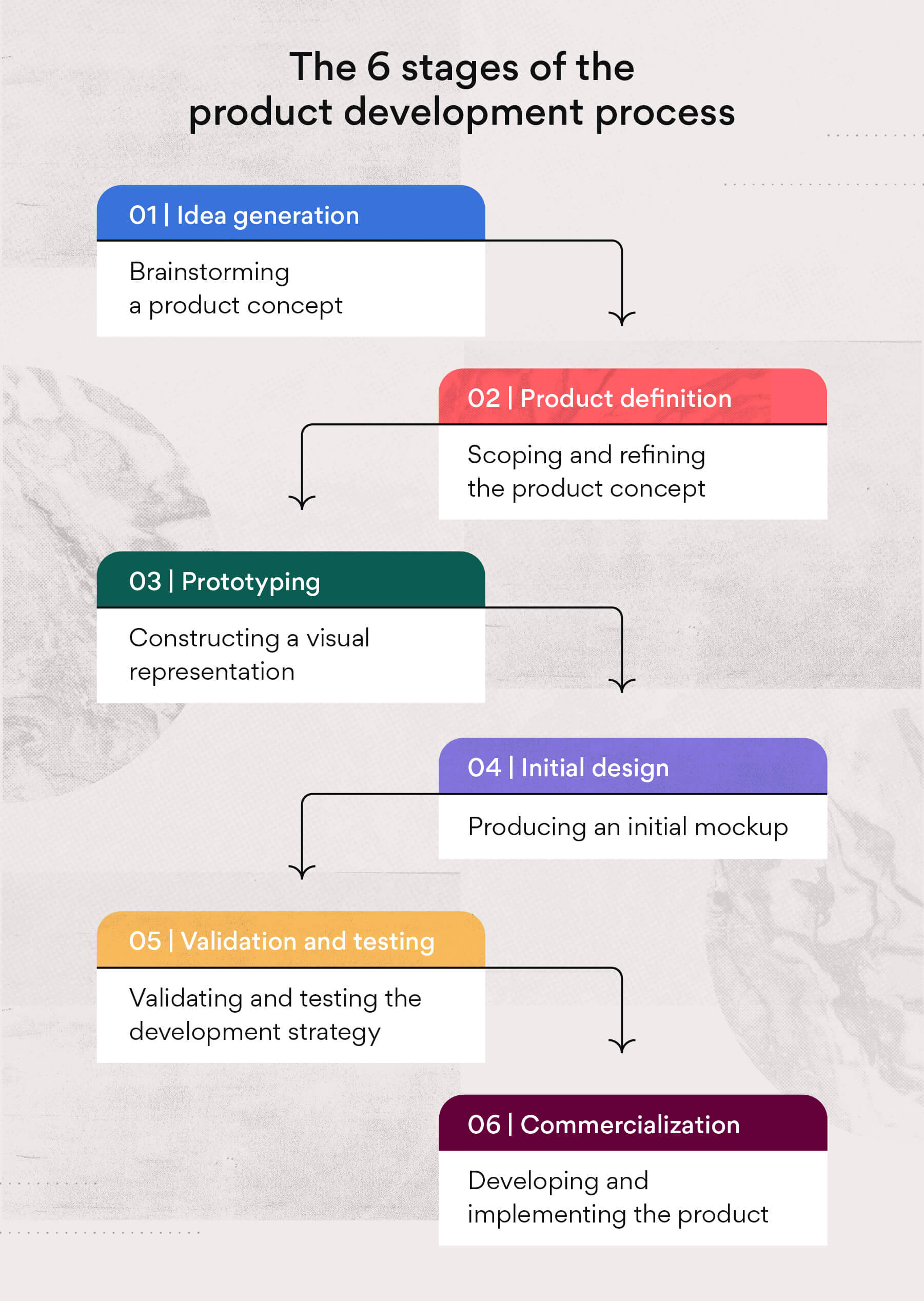
What Is Product Development The 6 Stage Process Asana

What Is Privileged Access Management Pam Read The Definition In Our Security Glossary Beyondtrust

Comments
Post a Comment